Application and Infrastructure Security Review
- Insurance (United Kingdom)
Challenge
- Crossjoin was challenged to review the security of an internal application hosted in the cloud that connects to a SaaS provider, with the aim of evaluating it:
- Application security
- Cloud infrastructure security
- Secure communication patterns
Solution
- Crossjoin carried out an in-depth security assessment of the client’s application and infrastructure. The goal was to identify vulnerabilities and provide expert recommendations to enhance the overall security of the client’s solution:
- Secure Code Review:
⇾ Detected vulnerabilities using Static Application Security Testing (SAST).
⇾ Performed Software Composition Analysis (SCA) to identify and mitigate risks in third-party dependencies.
⇾ Conducted a secure architecture review to evaluate the overall design.
⇾ Verified false positives from automated analysis tools to ensure accurate results.
⇾ Mapped findings against the OWASP Top 10 security risks to prioritize remediation efforts. - Cloud Infrastructure Security Review:
⇾ Analyzed the configuration of AWS products to identify potential misconfigurations.
⇾ Conducted benchmarking against industry-standard cloud security best practices to assess the robustness of the cloud infrastructure. - Secure Communication and API Request Handling Analysis:
⇾ Assessed the communication architecture to ensure compliance with secure design principles, including encryption and secure data transmission.
⇾ Tested the API to identify design flaws that could lead to security risks.⇾ Provided the client with state of the art DoS Testing and Chaos Engineering methodologies for testing and improving resilience
Results
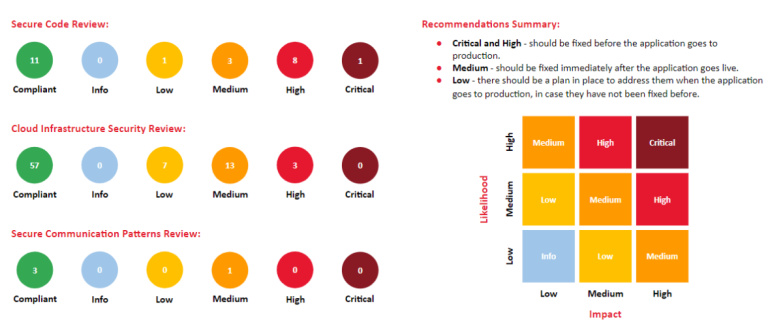
- Crossjoin provided the client with a detailed security report, which included:
⇾ Executive Summary: A high-level overview highlighting critical security risks and priorities within a risk matrix for easy decision-making.
⇾ Compliance Assessment: A thorough analysis of all assessed controls, categorizing them as compliant, non-compliant, or partially compliant.
⇾ Evaluation Methods: A reproducible description of the testing and evaluation process, along with the severity and potential impact of each vulnerability discovered.
⇾ Actionable Recommendations: Specific remediation plans for each identified issue, tailored to the client’s infrastructure and application setup.

Secure Development Lifecycle
Ensuring ongoing protection and detecting vulnerabilities early in the development process

Secure Code
Ensuring the application is built to resist attacks from the group up.

Hardened Security
Resisting attacks and minimizing potential security flaws.

Reduced risk of a breach
Reducing the likelihood of security breaches, disruptions and data loss.
Ready to start a project with us?
We have a team of professionals ready to respond to any challenge!
Talk to us!Are you up to the challenge?
Know how to become a Kenshi of IT and participate in exciting projects!
Join us!